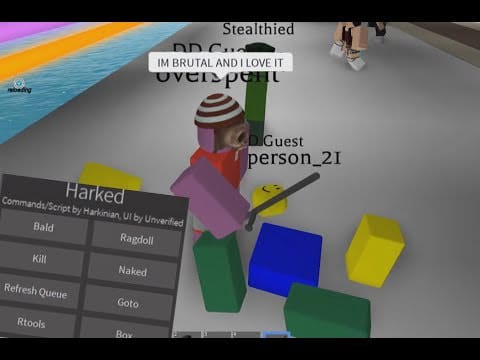
Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Security Orchestration Use Case: Automating Malware Analysis

PROUD-MAL: static analysis-based progressive framework for deep

Malware Analysis: Steps & Examples - CrowdStrike

Malware analysis index.html Malicious activity

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1

AV-TEST Confirms Skyhigh Security Service Edge Delivers Superior

Malware Analysis: Steps & Examples - CrowdStrike

Comprehensive Protection Strategies Against Cyber Threats
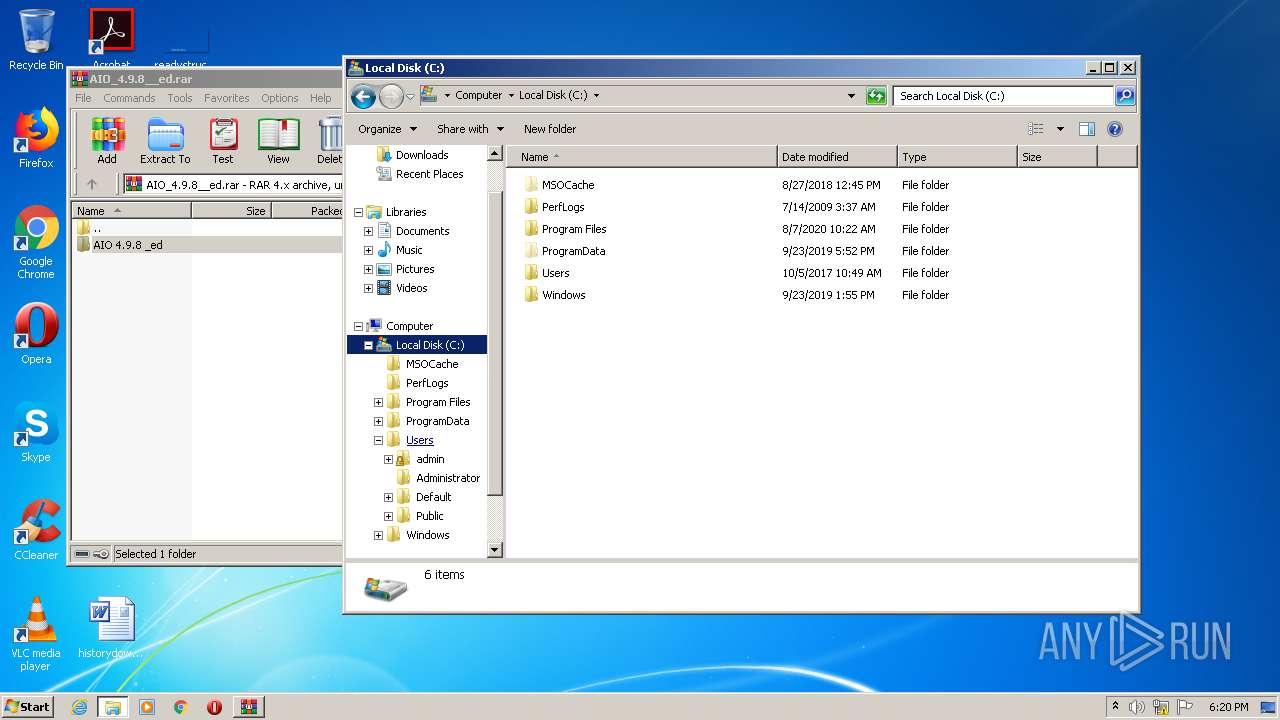
Malware analysis AIO_4.9.8__ed.rar Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike

Complex 'NKAbuse' Malware Uses Blockchain to Hide on Linux, IoT
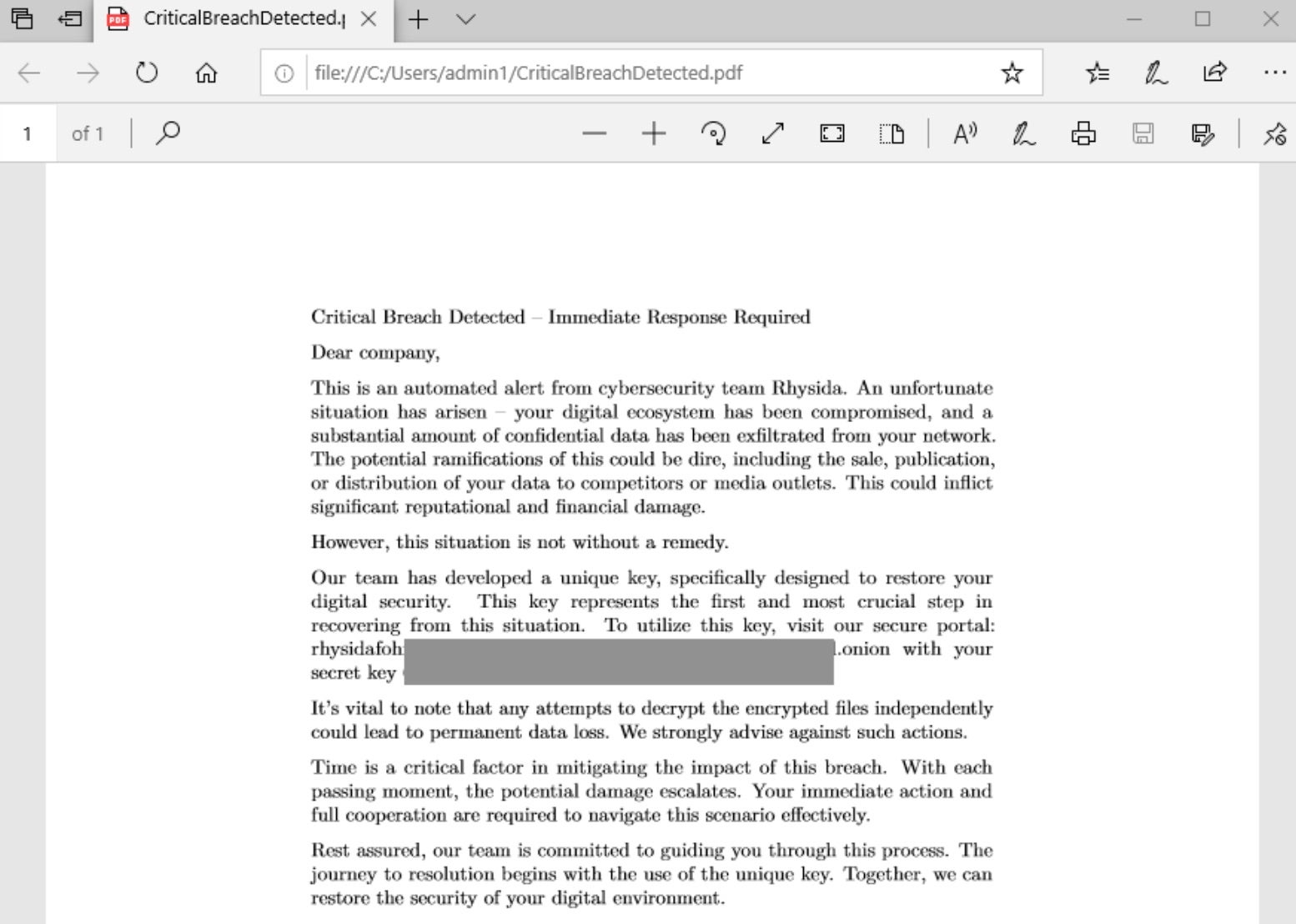
Rhysida - SentinelOne
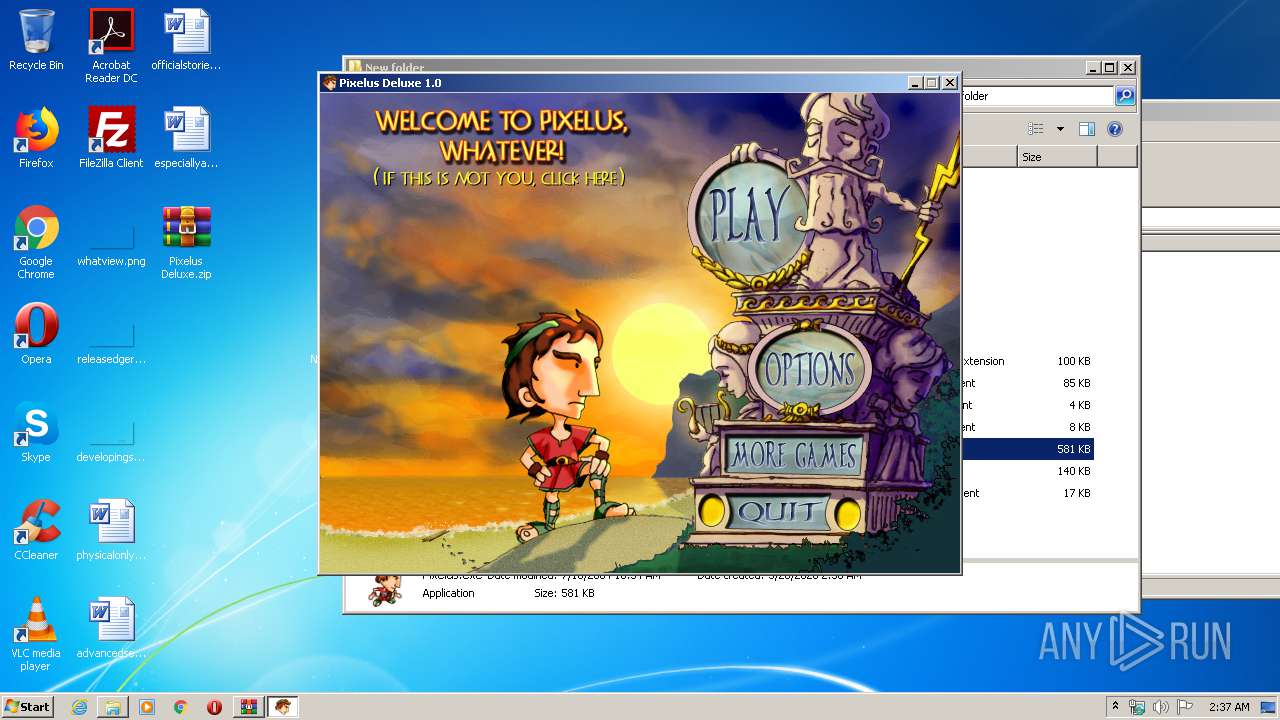
Malware analysis Pixelus Deluxe.zip Malicious activity

10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac
Malware analysis lockysample.bin.zip Malicious activity
de
por adulto (o preço varia de acordo com o tamanho do grupo)