Suspicious User Controls
Por um escritor misterioso
Descrição
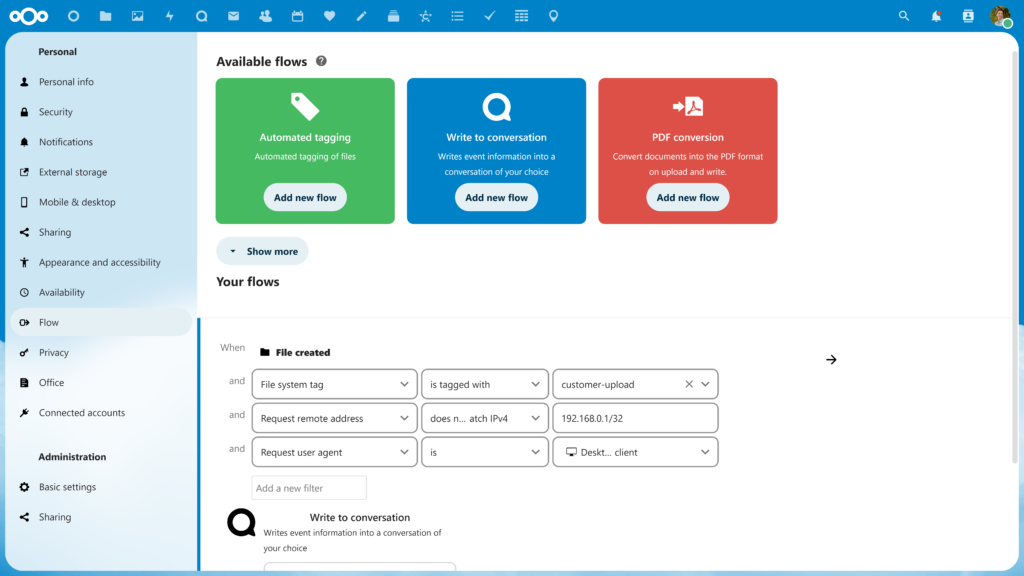
Nextcloud features that put you in control

Stop Stream Trolls On Twitch - Use Suspicious User Detection

Chapter 7 Activity: Testing and Monitoring Security
Tip 5: Search for related party transactions – MindBridge: English (US)
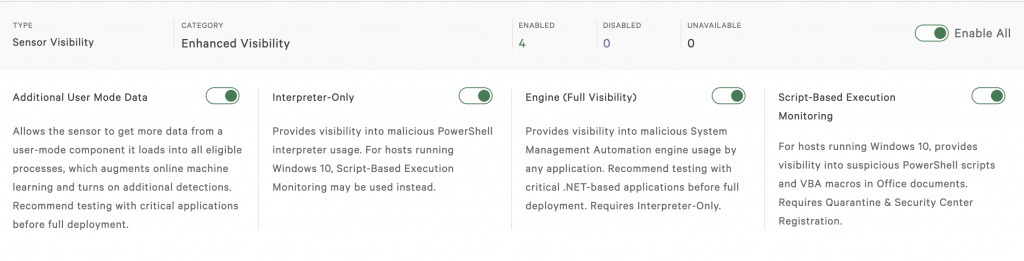
Blocking Fileless Script-based Attacks with Falcon Script Control
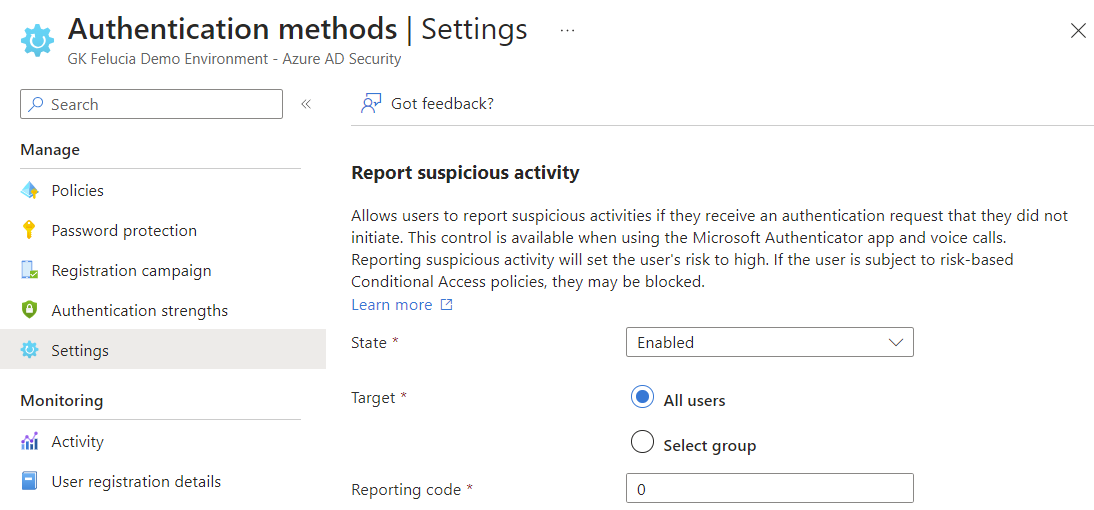
Microsoft Entra MFA Fraud Deep Dive, by Christopher Brumm

Detect Potentially Suspicious Activity In Teams With Cloud App Security – Sam's Corner
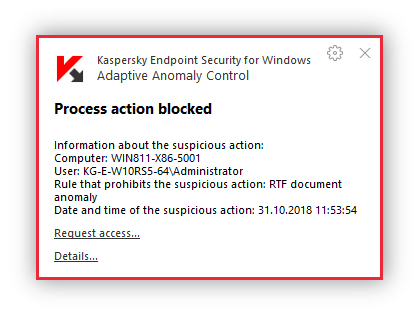
Adaptive Anomaly Control
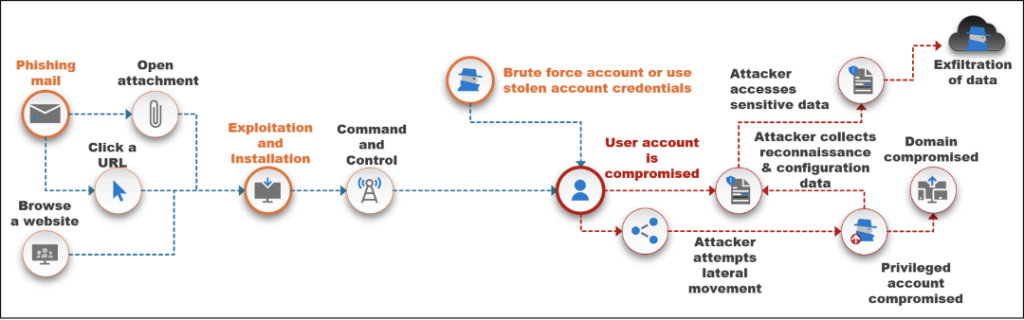
Identity is the New Perimeter - Critical Start

GSPBC-1044: Lateral Movement - Taint Shared Content - GuardSight, Cybersecurity as a Service
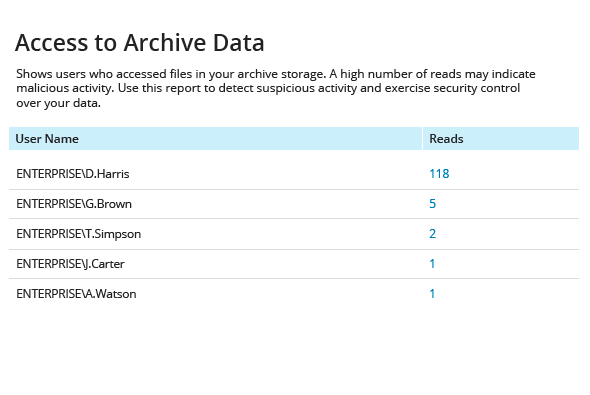
Detect and Investigate Suspicious User Behavior
Content control – Access to users correspondence add-on, Communications - Marketplace — PG Dating Pro
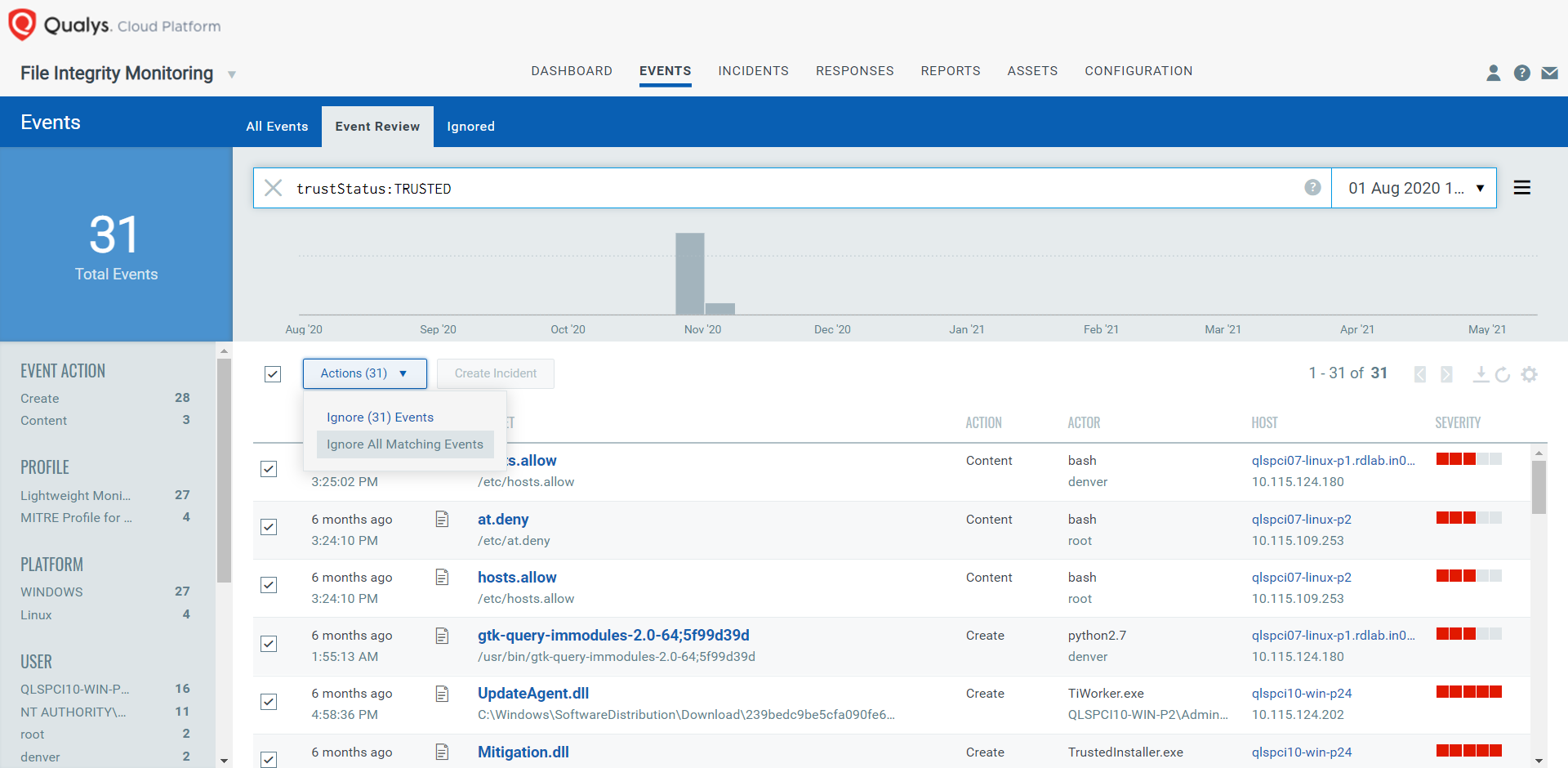
Reinforce Defense with File Reputation and Trusted Source Intelligence in Qualys FIM

PDF] Suspicious-Taint-Based Access Control for Protecting OS from Network Attacks
Battling Ban Evasion with Machine Learning
de
por adulto (o preço varia de acordo com o tamanho do grupo)