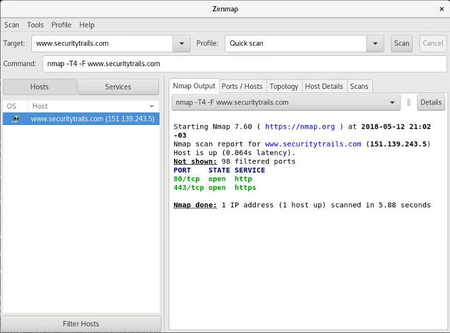
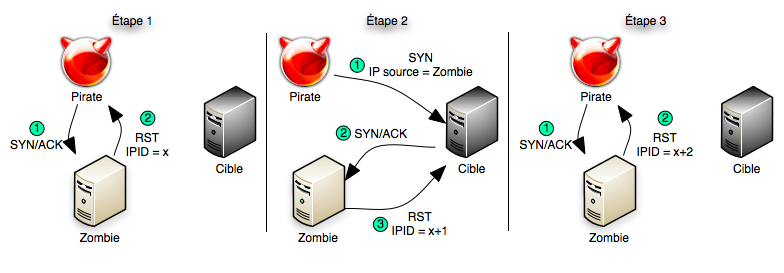
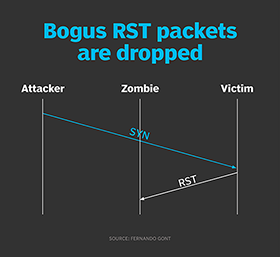
TCP Idle Scan (-sI) Nmap Network Scanning
Por um escritor misterioso
Descrição
How hackers use idle scans in port scan attacks
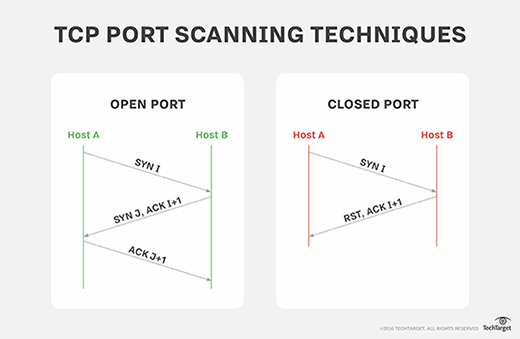
What is SYN scanning and how does it work?
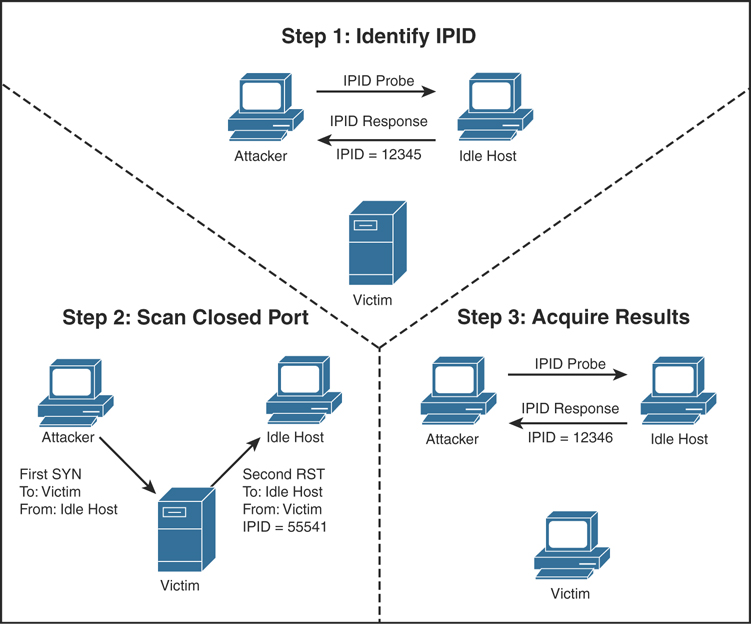
Scanning, Footprinting, Reconnaissance, and Scanning
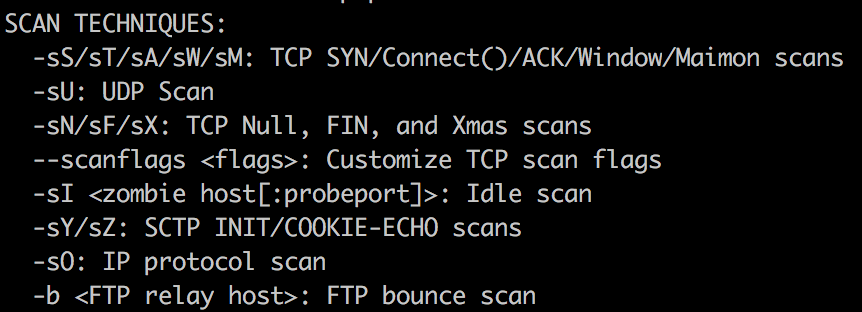
Deep Dive Into Nmap Scan Techniques, by PenTest-duck

How to hide yourself using Idle scan (-sl) - Port scanning tutorial
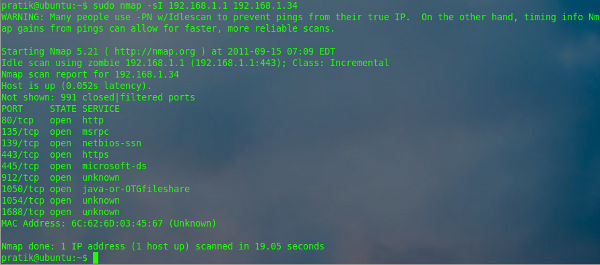
Understanding Nmap Commands: In depth Tutorial Part II
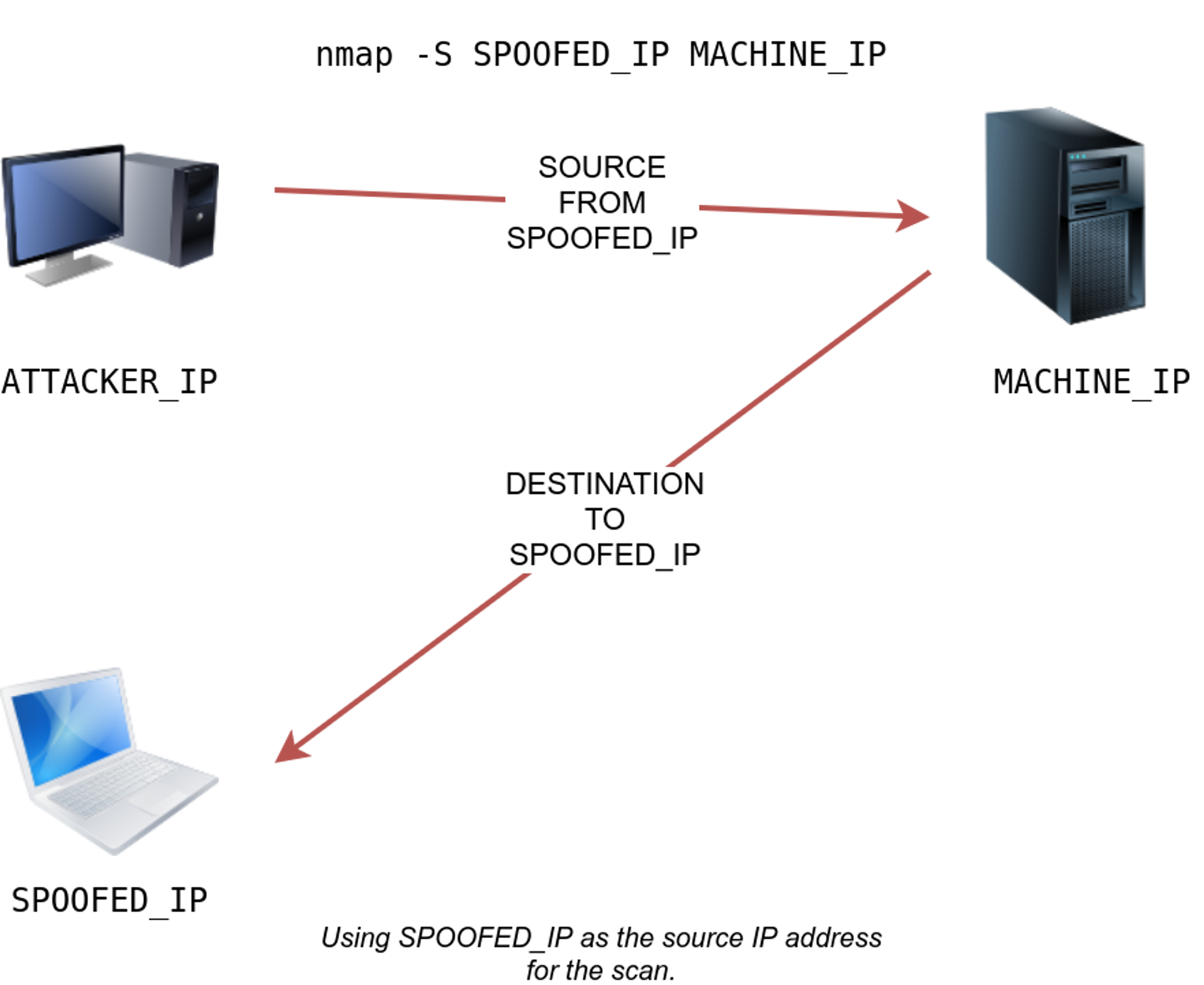
The Ultimate Guide to Port Scanning using Nmap
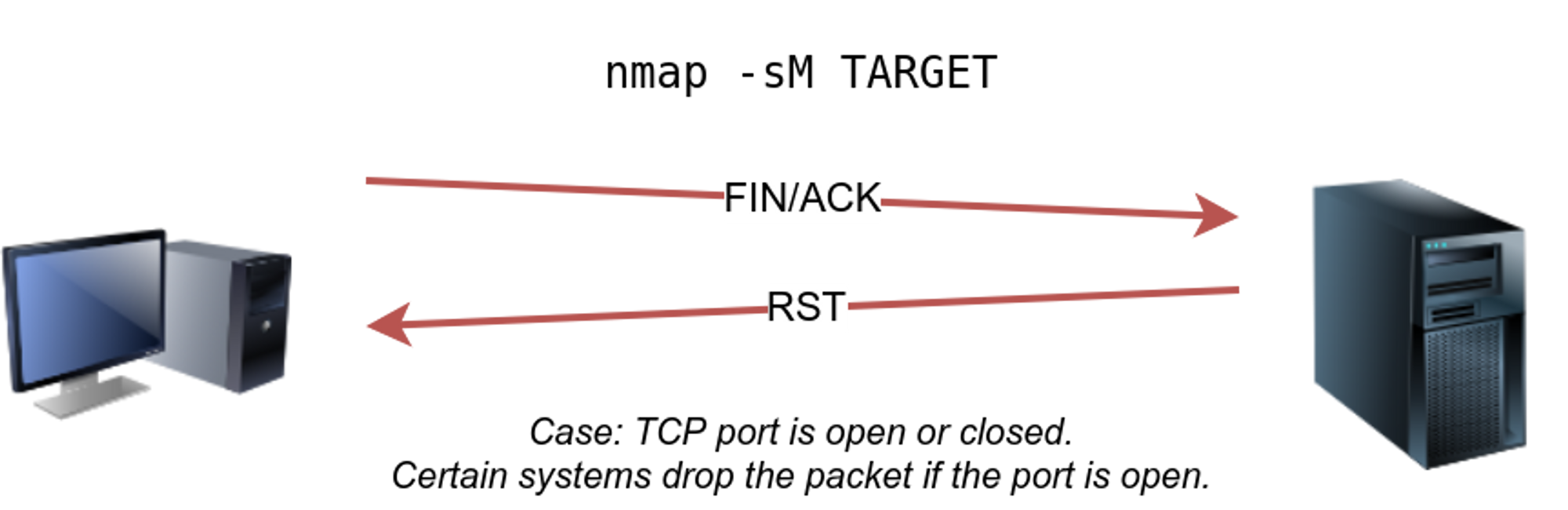
The Ultimate Guide to Port Scanning using Nmap

Network Mapper (NMAP)
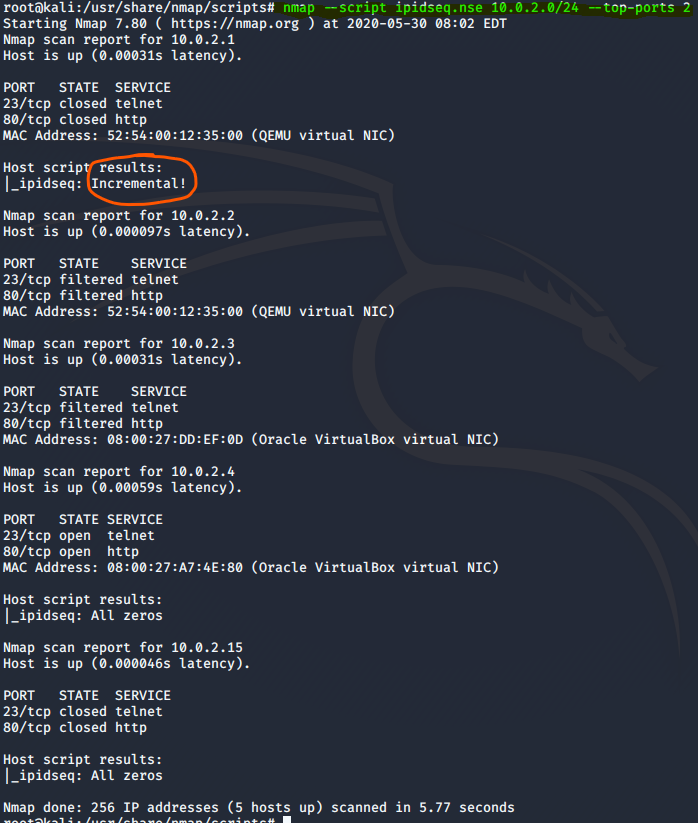
End]Network Vulnerability and Scanning: Other NMAP Scans (NULL,FIN,XMAS,ACK, IDLE), by Koay Yong Cett
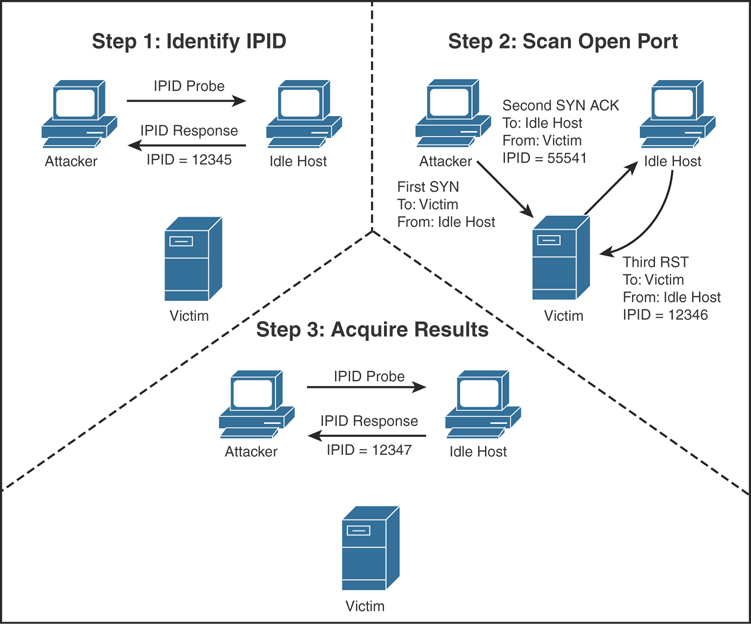
Scanning, Footprinting, Reconnaissance, and Scanning

Nmap cheat sheet: From discovery to exploits, part 2: Advance port scanning with Nmap and custom idle scan
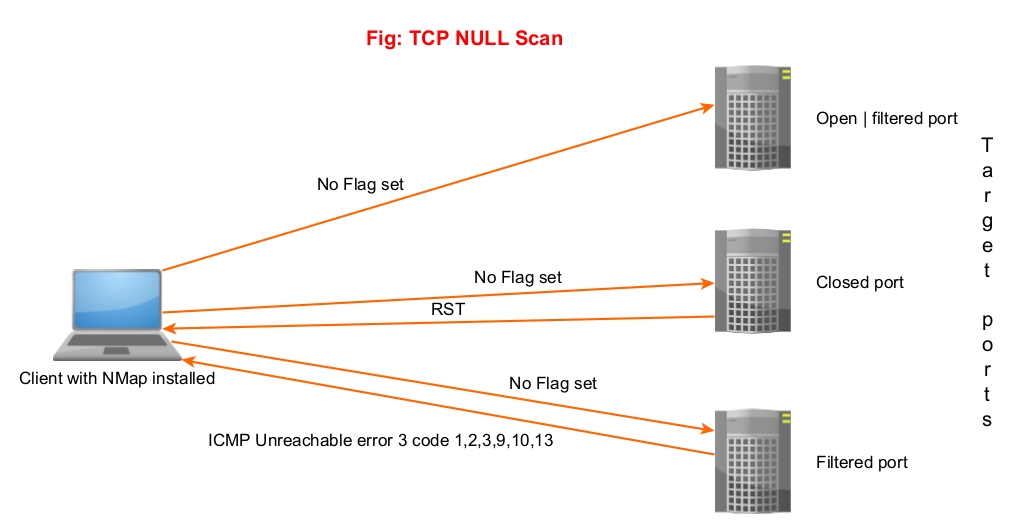
Nmap Archives - Hackercool Magazine

Port Scanning - an overview
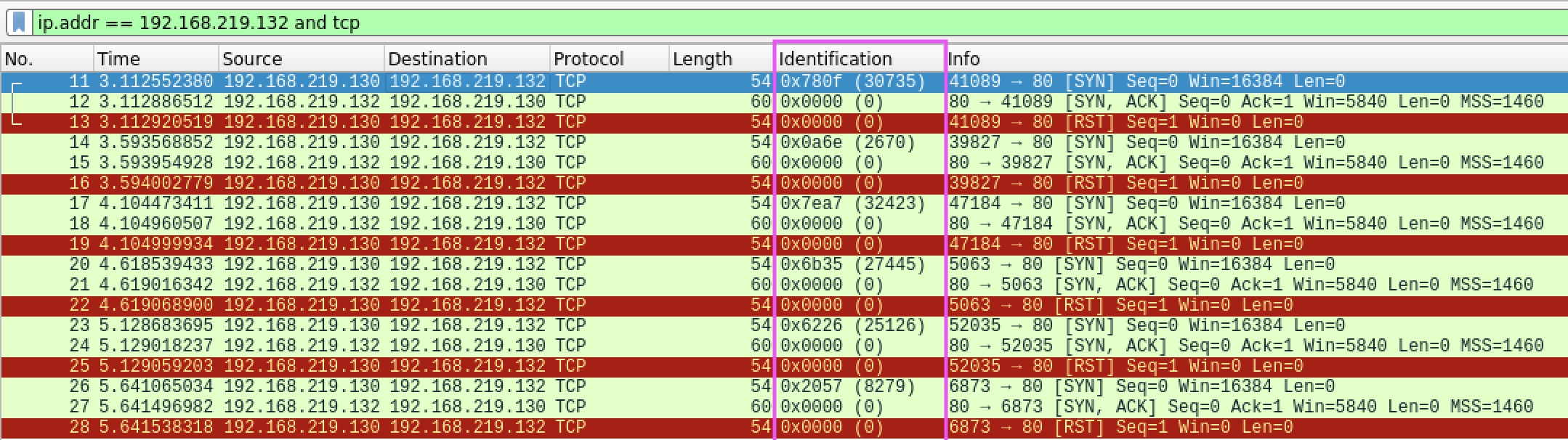
Pentesting - Nmap Stealth Scan
de
por adulto (o preço varia de acordo com o tamanho do grupo)