Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Descrição
Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

Malware: Types, Examples, and How Modern Anti-Malware Works

Guarding Against the Unseen: Investigating a Stealthy Remcos

How Hackers Use Social Engineering to Spread Dridex Malware

The Growing Threat of Fileless Attacks: Insights on Cybersecurity

Telegram Bot Telekopye Powering Phishing Scams from Russia

10 Malware Examples and 6 World Famous Attacks
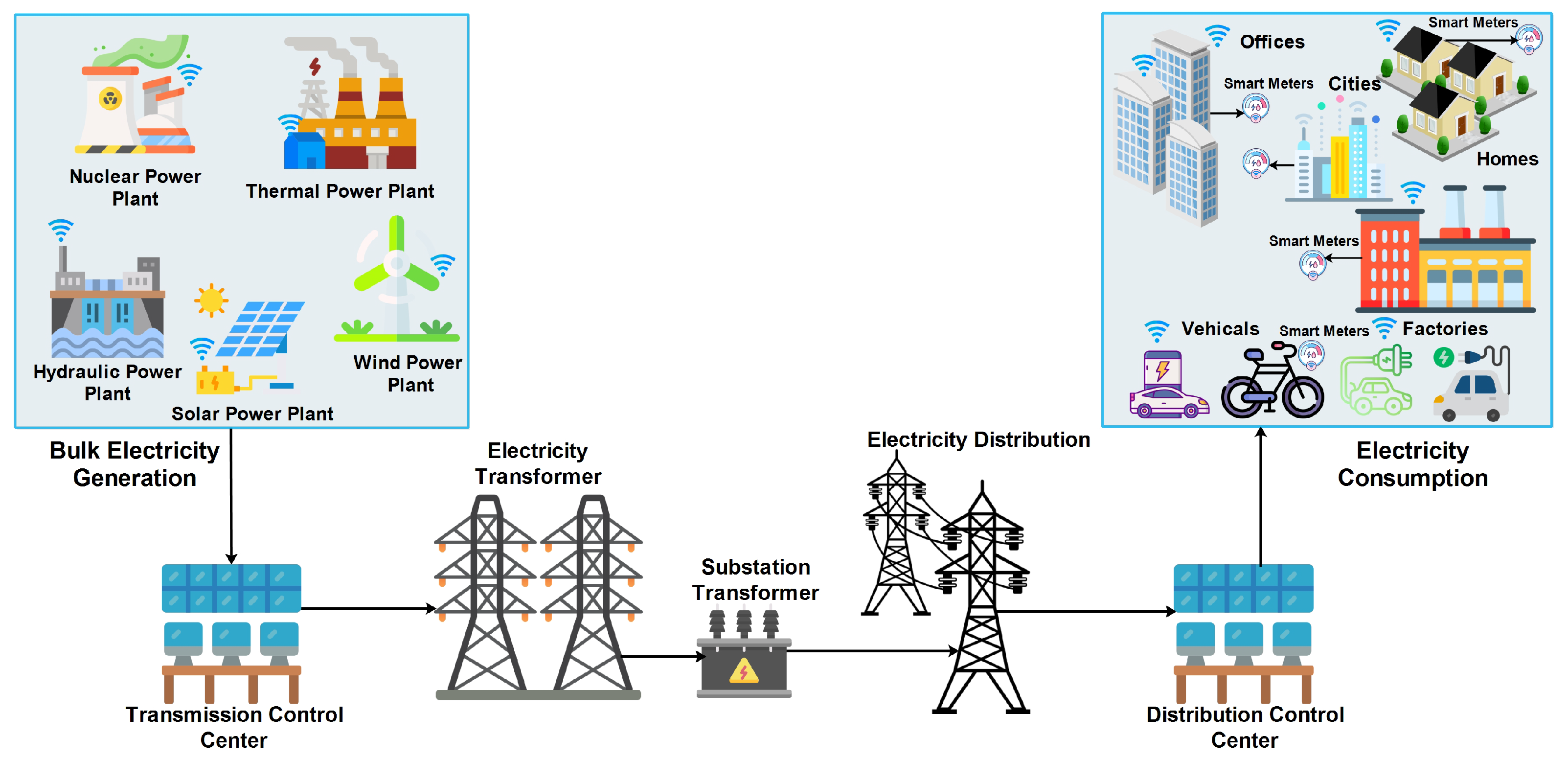
Energies, Free Full-Text

Artificial Intelligence And Cybersecurity: For Good Or Evil?
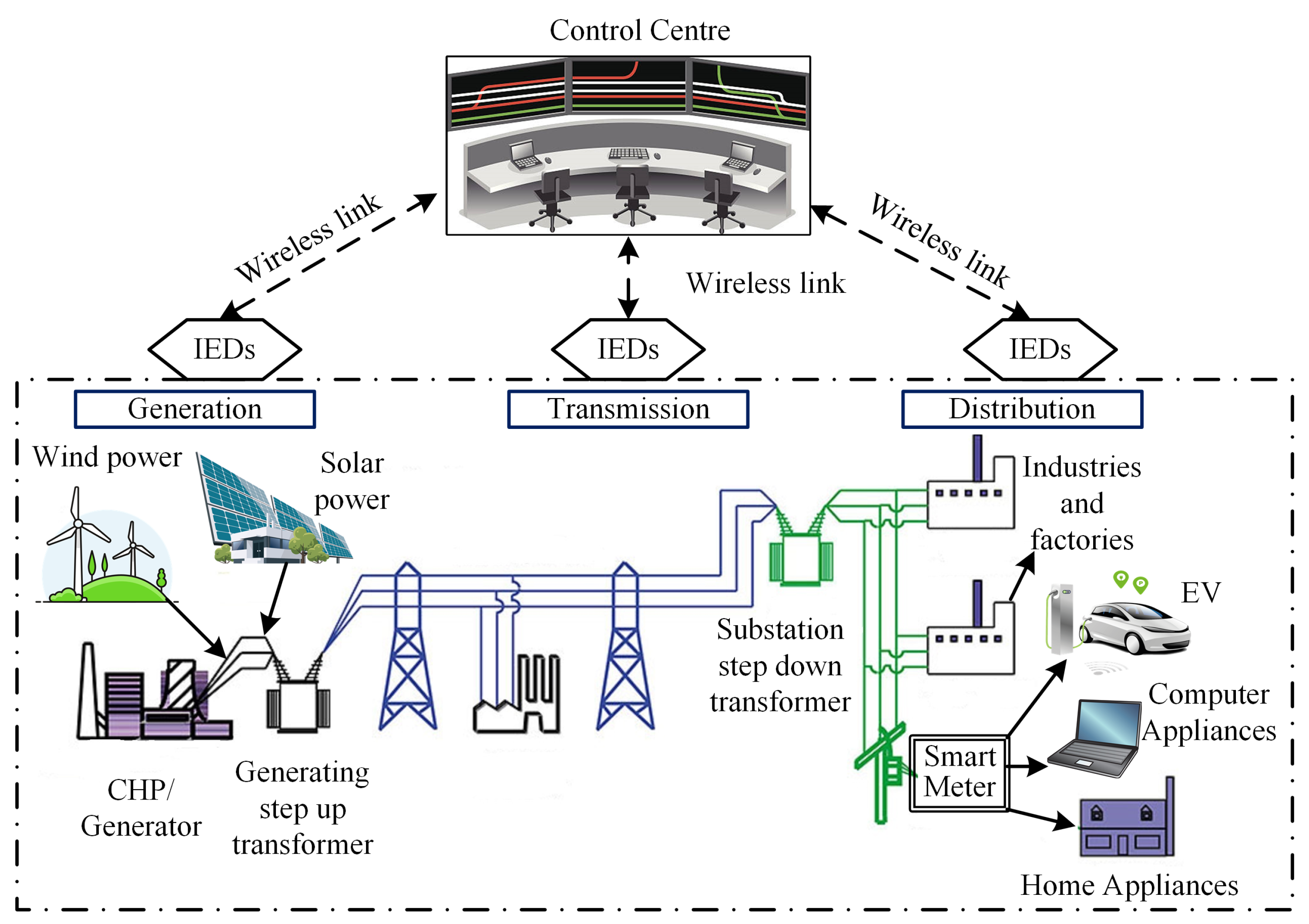
Electronics, Free Full-Text
de
por adulto (o preço varia de acordo com o tamanho do grupo)